Here we are again with another Vulnerability related to the SSL/TLS Ecosystem called the ROBOT Attack (robotattack.org) and that usually means the NetScaler is also affected or you need to change some part of your SSL/TLS Configuration.
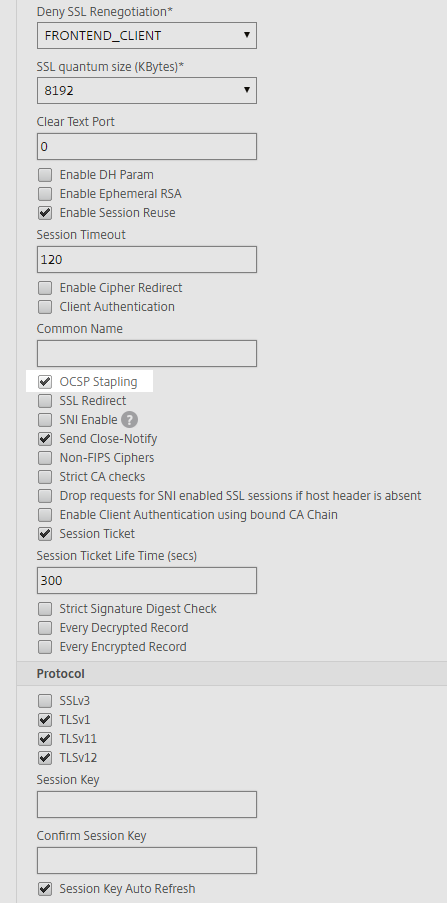
Besides updating your NetScaler Firmware to one of the latest Builds (see CTX230238 for fixed Builds) you need to remove all Ciphers starting with TLS_RSA from your Cipher List. Below is a Cipher List where all the Ciphers with RSA Encryption are removed to prevent the ROBOT Attack.
You could alternatively also use the Modern Compatibility Cipher List:
https://docs.citrix.com/en-us/receiver/windows/4-7/configure/ica-import-icaclient-template-v2.html
Important Note: Only Citrix Receivers for Windows starting with Version 4.7 or higher can connect to your published Desktops/Applications after applying the new Cipher List. This is because ECDHE Cipher Support was first implemented with Receiver 4.7 and we have removed all the other supported Ciphers starting with TLS_RSA_*.
You can see a List of supported Ciphers for the Citrix Receiver starting with Version 4.7 below:
https://docs.citrix.com/en-us/receiver/ios/7/secure-communications.html
Update #1: I had to learn the hard way that the Citrix iOS Receiver 7.4 can't work with the posted Cipher Lists because the iOS Receiver only supports Ciphers starting with TLS_RSA_*.
Hopefully Citrix will soon release a new Version with additional Cipher Support.
Update #2: The Problem with the Citrix iOS Receiver has been fixed in the 7.5 Version. You can now use the new Cipher List with the latest iOS and Android Receivers.
Verification:
As always test your updated Configuration with the SSLLabs Test or use the Comodo SSL Analyzer.
Feedback and Comments is as always very welcome.