Starting with NetScaler 11.1 Build 51.21 the NetScaler now supports OCSP Stapling. Yay!
For more in-depth Information about OCSP Stapling and why you should enable it I recommend reading Scott Helme's Blogpost about OCSP.
But let's get started on how to configure the NetScaler to enable OCSP Stapling (the GUI way).
Requirements
- NetScaler 11.1 Build 51.21 or later
- Outbound Firewall Rule to allow the NetScaler Subnet IP (SNIP) to communicate with the External OCSP Responder on Port 80 (HTTP).
- Existing SSL/TLS Certificate with embedded OCSP Extension (AIA Extension)
- Working DNS Resolution on NetScaler for "external" URLs
Configuration
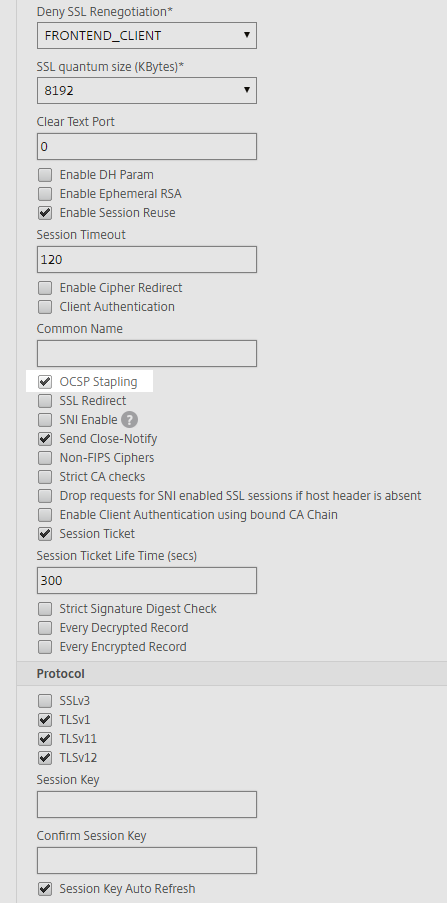
First thing is we need to enable the OCSP Stapling Feature on the SSL Profile in case you are using SSL Profiles or the SSL Default Profiles to configure your SSL/TLS Settings. Otherwise you have to enable the OCSP Stapling Feature in the SSL Parameters for every vServer.
You can find it in the GUI under System -> Profiles -> SSL Profile:
You can choose to create a new SSL Profile (FrontEnd) or edit one of the existing ones, for example the ns_default_ssl_profile_frontend Profile. In my example I'm editing the ns_default_ssl_profile_frontend Profile and enabled the OCSP Stapling checkmark and afterwards saved the Configuration.
Next Step is to create a new OCSP Responder. After upgrading to the latest NetScaler Build you will notice that there are one (or more) OCSP Responders automatically generated with the INTERNAL_ Prefix when checking under Traffic Management -> SSL -> OCSP Responder.
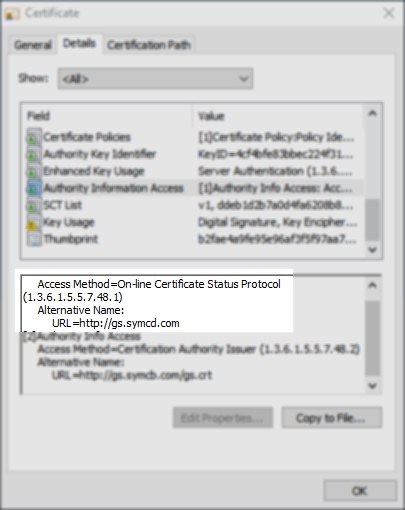
These are generated automatically for every OCSP URI found in the Certificates currently imported into the NetScaler. In my Example I'm using a Certificate from RapidSSL (GeoTrust) which is owned by Symantec and hence the *.symcd.com OCSP URI.
You can check the OCSP URL by looking at your Certificate under the AIA Extension.
You can't edit the auto-created INTERNAL_ OCSP Responders so I opted to "duplicate" the INTERNAL_ OCSP Responders and create new ones where I configured some specific Settings.
I disabled the "Nonce" Checkmark and checked the "Trust Responses" Option.
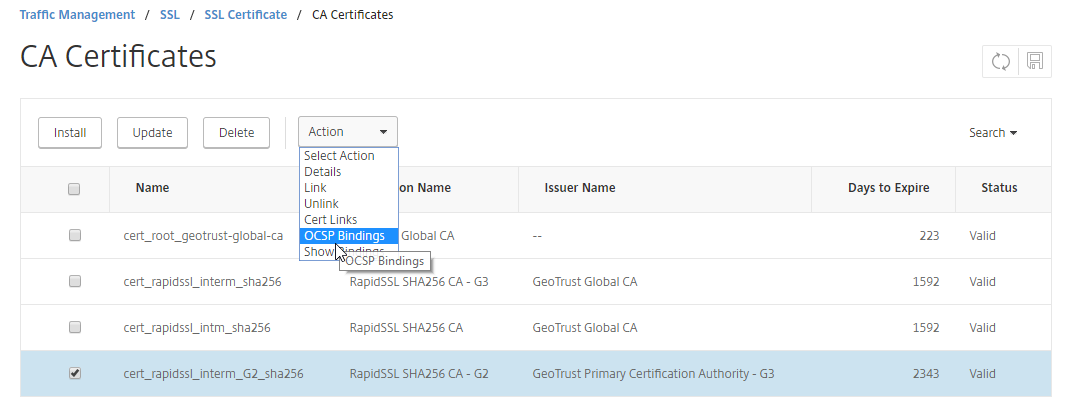
After saving your new OCSP Responder we need to bind it to the CA Intermediate Certificate (not the SSL/TLS Certificate) which issued your SSL/TLS Certificate. Navigate to Traffic Management -> SSL -> Certificates -> CA Certificates and bind the newly created OCSP Responder to the Intermediate CA Certificate.
Last Step to configure is to bind the SSL Profile with enabled OCSP Stapling to your vServer. Or enable the OCSP Stapling Option under SSL Parameters if you are not using SSL Profiles / SSL Default Profiles.
Check your Configuration
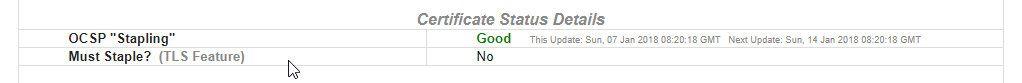
Last Step is to check if OCSP Stapling is working as intended. You can use SSLLabs, Comodo SSL Analyzer or OpenSSL CLI to check it.
OpenSSL: (Command: openssl s_client -connect example.com:443 -tlsextdebug -status)
Troubleshooting:
If none of the Test Tools are reporting the successful OCSP Stapling Support make sure to check that the NetScaler can reach the OCSP Responder on Port 80 (via HTTP) through a possible Firewall. The Traffic should originate from the Subnet IP Adress (SNIP) or NetScaler IP (NSIP).
Also make sure that the NetScaler can resolve the OCSP URI and that the DNS Resolution is working. As most (if not all) Public CAs are using a Content Deliver Network (CDN) for their OCSP Responders configuring a OCSP Responder with a IP is not recommended because the IPs on CDNs might change quite often.
From the NetScaler BSD Shell (not the NetScaler CLI) you can run the following Command which could indicate where the Problem lies: nsconmsg -d stats | grep ocsp
The Counter ssl_err_ocsp_http_callout_failed for example could indicate a Problem reaching the OCSP Responder because of Firewall Problems.
Blogpost Changelog:
#1 - 09.01.2017 - Initial Draft
#2 - 13.01.2017 - added Troubleshooting Command for OCSP Counters